COMMS FOR A CAUSE
At the intersection of communications and digital security, we create the shield and megaphone of movement infrastructure, transforming visibility into safety, and stories into people power.
Because Strengthened Movements Strengthen Movements.


Redistributing Power, Collectively
Whether you're a donor, funder, or movement-rooted activist, here is everything you need to know about how our partnership can build safer, stronger, and sustainable narrative and tech power for change.
Our Approach


Feminist, Holistic, and Radical Resource Redistribution (FHR3)
The FHR3 model is our way of treating communications and digital security as core movement infrastructure. It’s a redistribution model that goes beyond money, combining strategic communications, digital security, and trauma-aware accompaniment into one political methodology. Through FHR3, we walk alongside movements for a year, co-creating the narratives and protection systems that build for them the infrastructure and pathways for global influence. We do this through 4 accompaniment approaches:


Micro Grants
Our micro funding model is designed to catalyze immediate, strategic investment in communications and digital security without creating dependency or administrative burden. Each selected organization receives a flexible micro grant intended specifically to seed or strengthen their capacity in these two critical areas.


Communications and Storytelling
Our communications accompaniment is embedded in a one-year, strategic partnership with each selected organization. Over the course of the year, we walk alongside organizations to co-develop communications tools, narrative infrastructure, and storytelling processes that are aligned to their work, movement ecosystem, and safety concerns.


Digital Security and Justice-Tech Infrastructure
For many movements, being seen is inseparable from being targeted. Our digital security and justice-tech accompaniment ensures that organizations are not only visible but protected. Over a one-year cycle, we work alongside movements to integrate security into the very fabric of their organizing.


Linking and Learning
Movements must not only strengthen their own infrastructure, they must also be present where global agendas on communications and digital security are being shaped. As part of our one-year accompaniment cycle, we ensure that organizations are not left out of these critical arenas by bringing them as C4AC delegation to global and regional convenings on communications, digital rights, and security.
Our Theory of Change
We believe that in an age of narrative warfare, surveillance capitalism, and digital repression, movements need new forms of infrastructure; ones that allow them to be visible without being vulnerable, resourced without being extractable, and powerful without being underprepared for it.
Our Theory of Change
We believe that in an age of narrative warfare, surveillance capitalism, and digital repression, movements need new forms of infrastructure; ones that allow them to be visible without being vulnerable, resourced without being extractable, and powerful without being underprepared for it.



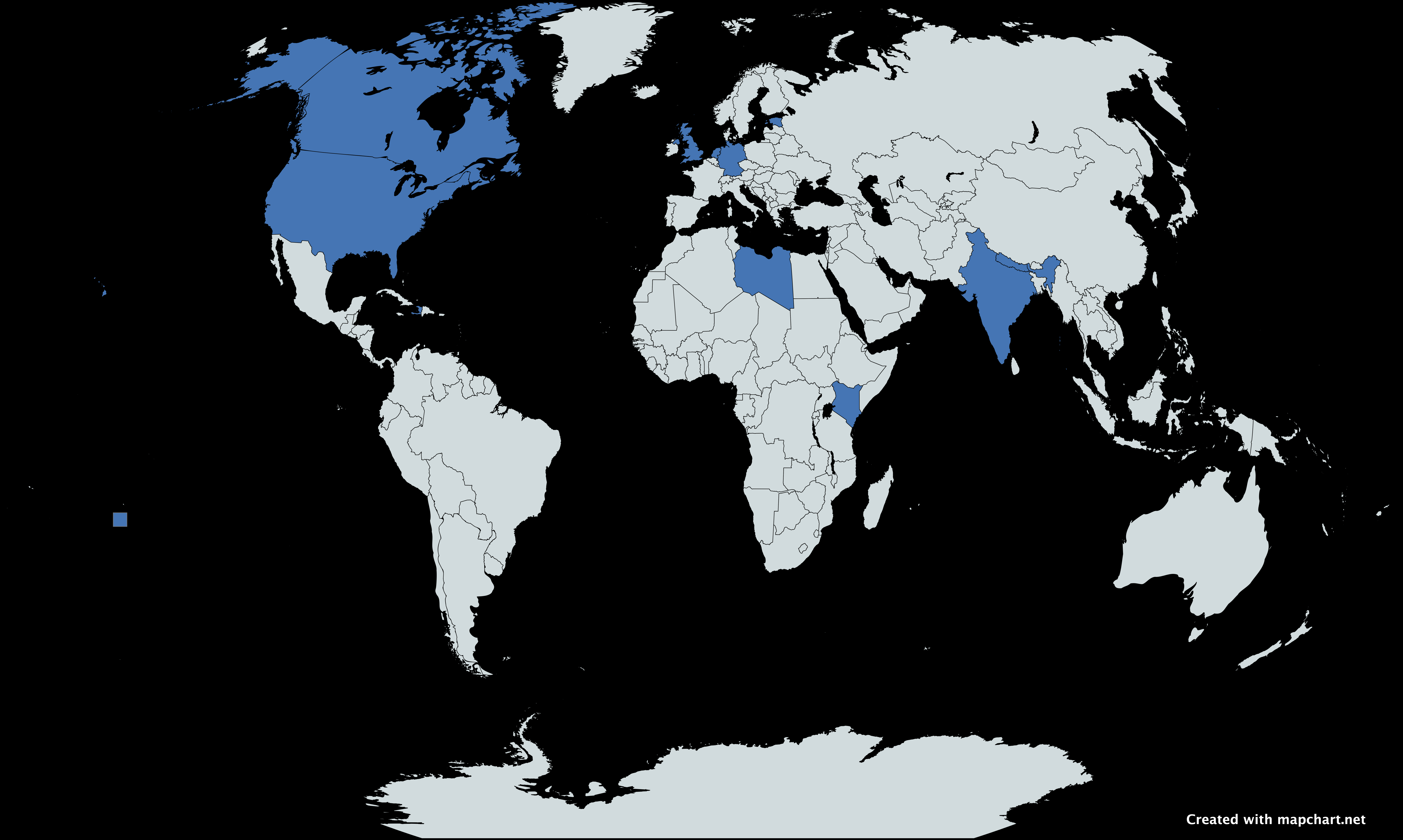
Our Partners Across The World